Why Modern Access Control is a Business Essential

Controlled door access systems have evolved far beyond the simple lock and key. Modern businesses need smart, reliable security solutions that protect assets while streamlining daily operations.
Quick Answer for Businesses Choosing Access Control Systems:
- Cloud-based systems: Best for multi-site operations, remote management, and scalability
- On-premise systems: Ideal for strict compliance needs and maximum data control
- Key components: Readers, controllers, electronic locks, credentials, and management software
- Essential features: Real-time monitoring, audit trails, mobile credentials, and integration capabilities
- Installation time: 30-60 minutes per reader, plus 2-5 hours for software setup
The construction industry faces unique security challenges. Job sites have valuable equipment, multiple contractors need temporary access, and traditional keys create operational headaches. Modern access control solves these problems by giving you complete control over who enters your facilities and when.
Today's systems integrate seamlessly with other security technologies like video surveillance and alarm systems. They provide detailed audit trails for compliance, eliminate the cost and risk of lost keys, and can be managed remotely from anywhere.
This guide will help you understand the key components of access control systems, compare your deployment options, and choose the right solution for your business needs. Whether you're securing a single office or managing multiple construction sites across Texas, the right access control system becomes a strategic business tool - not just a security measure.
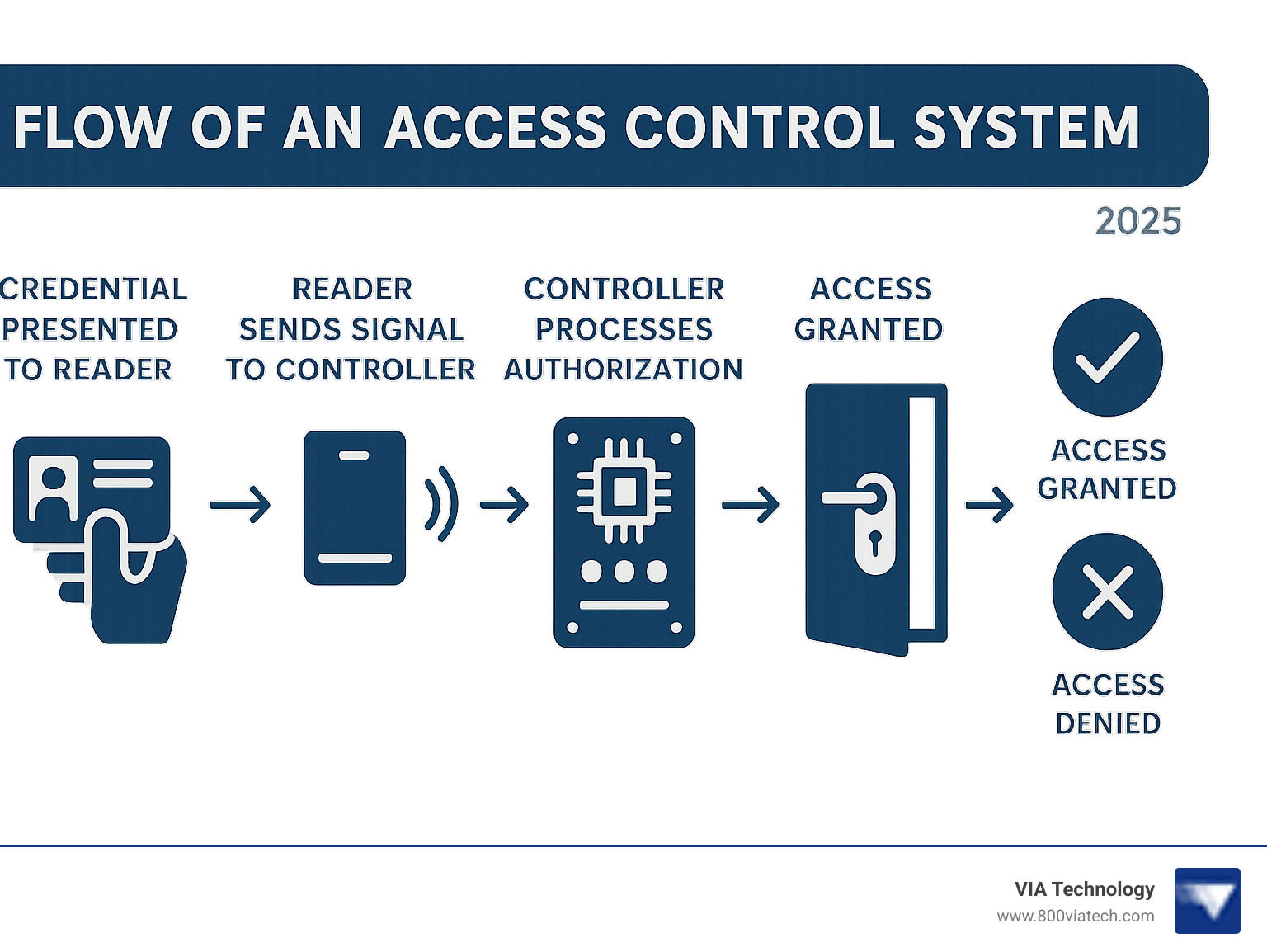
The Anatomy of Controlled Door Access Systems
When we talk about controlled door access systems, we're discussing a sophisticated blend of hardware and software working in harmony to manage entry and exit points. It's about knowing who is where, when, and having the power to grant or revoke access instantly. This synergy vastly improves physical security, offering a level of control that traditional locks simply can't match.
The Hardware: What Makes the Door Smart?
At the heart of any controlled door access system is a collection of interconnected hardware components that create a secure, smart portal. These elements are designed for reliable performance and seamless integration.
The "brain" of the operation is the Access Control Unit (ACU). This central command panel makes all entry decisions, authorizing data from the reader and triggering the lock. ACUs are scalable, managing anything from a single door to thousands across multiple construction sites, and can integrate with other security systems via input/output ports.
Entries are secured with electronic commercial door locks. These specialized locks are controlled electronically and include electric strikes, which release the door latch, and magnetic locks (maglocks), which use immense force to hold a door shut. Electrified push bars can also be integrated, all triggered by the ACU.
Readers are the interface where users present credentials. Options range from simple PIN keypads to card readers (RFID/NFC) and advanced biometric readers that scan fingerprints or facial structures for improved security.
Larger facilities often use specialized controllers for doors and elevators for granular control over specific floors or restricted areas. For example, dormakaba's Keyscan controllers can regulate access to interior/exterior doors and secure elevator floors, requiring credentials for use. These units can leverage existing architecture and software, allowing for mixed installations that increase security and minimize costs.
The Credentials: Modern Keys for a Modern Workforce
Modern controlled door access systems offer a variety of credentials to suit different business needs, moving far beyond traditional metal keys.
Key Cards & Fobs are the most common digital "keys." Using RFID or NFC technology, these portable devices are cost-effective, easy to issue, and can be quickly deactivated if lost or stolen.
The future of access is mobile. Mobile Credentials use smartphones and smartwatches to grant access via Bluetooth or NFC. With over 85% of Americans owning a smartphone, businesses can avoid issuing physical cards. Credentials can be managed remotely and are secured by the phone's existing protections. Employees can use their iPhone or Apple Watch to access doors and elevators, integrating seamlessly with existing systems. Learn more about employee badge in Apple Wallet integration >> This simplifies management for multi-site businesses, eliminating the need to restock physical cards.
For the highest security, Biometrics use unique biological traits like fingerprints or facial recognition for authentication. These are nearly impossible to replicate or lose. For sensitive areas like server rooms or data centers, we recommend multi-factor authentication (MFA), which combines biometrics with another credential (like a PIN or mobile key) for layered protection.
These modern credentials, from cards to digital badges, are easy to issue, adjust, or revoke, ensuring your property remains secure.
The Software: The Central Command Center
While the hardware handles the physical interaction, the software is the central command center that orchestrates the entire controlled door access system. It's where you define permissions, monitor activity, and manage the flow of people throughout your facility.
This sophisticated management platform allows administrators to:
- Set user permissions: Determine exactly who can access which doors. For example, a construction site manager might have access to all areas, while a specific contractor might only have access to their designated work zone.
- Define access levels: Create groups of users with similar access needs, simplifying management.
- Establish scheduling: Grant access only during specific hours or days, perfect for managing contractor schedules or after-hours cleaning crews.
- Generate reporting and audit trails: This is a critical feature for businesses. The software carefully logs every entry and exit attempt, noting the user, time, and location. These detailed report logs and audit trails are invaluable for security investigations, compliance requirements, and verifying who accessed specific readers. They can even be integrated with video security cameras to locate relevant footage.
- Enable remote access capabilities: Many modern systems allow administrators to manage the system from anywhere with an internet connection, providing unparalleled flexibility for businesses with multiple locations or managers on the go.
The software ensures that your access control system is not just a barrier but an intelligent management tool, streamlining daily operations and bolstering your overall security posture.
Cloud vs. On-Premise: Choosing Your System's Foundation
When implementing controlled door access systems, a key strategic decision is choosing between a cloud-based or on-premise solution. This choice impacts your budget, operations, and ability to scale.
Think of on-premise as owning a generator and cloud-based as plugging into the power grid. Both work, but their infrastructure is fundamentally different.
Here's how these two approaches stack up:
| Criteria | On-Premise Access Control | Cloud-Based Access Control |
|---|---|---|
| Initial Cost | Higher (hardware, software licenses, installation) | Lower (subscription fees, minimal hardware upfront) |
| Ongoing Cost | Maintenance, upgrades, IT staffing, energy | Subscription fees (often includes maintenance/upgrades) |
| Scalability | Requires hardware upgrades, can be complex/costly | Highly scalable (add/remove users/doors easily via subscription) |
| Maintenance | Managed internally (IT staff, manual updates) | Managed by provider (automatic updates, remote support) |
| Remote Access | Requires VPN or specific configurations | Built-in (access from any internet-connected device) |
| IT Resources | Significant (servers, network, security, administration) | Minimal (web browser, mobile app) |
On-premise systems keep all data on local servers in your building, giving you complete control. This is ideal for businesses with strict compliance requirements or highly sensitive information. The trade-off is that your IT team is responsible for all maintenance, updates, and troubleshooting, which can be a challenge for companies with multiple job sites.
Cloud-based systems run on the provider's servers and are accessible via the internet. This Software-as-a-Service (SaaS) model offers incredible flexibility and scalability, especially for businesses with multiple locations. A project manager in Dallas can grant access to a contractor in Austin from their phone. Adding new doors or users is as simple as adjusting a subscription.
Cloud systems also integrate seamlessly with other technologies, like our Networking Systems, to create a unified ecosystem. The provider handles updates and system health, so you always have the latest features without IT headaches. While there are ongoing subscription costs, they are predictable and often more budget-friendly than maintaining aging on-premise hardware.
At VIA Technology, we help Texas businesses choose the right foundation for their controlled door access systems based on their specific needs and growth plans, ensuring long-term success.
From Blueprint to Operation: Key Features, Installation, and Benefits
When you're ready to implement controlled door access systems, success comes from a holistic approach that considers the entire system lifecycle, from features and benefits to installation and maintenance.
Essential Features and Integration Capabilities
The best controlled door access systems share several must-have features:
- Remote management: Grant or revoke access from anywhere, a crucial feature for managing multiple sites like construction projects. A manager in Dallas can instantly give a contractor access to a site in Austin.
- Real-time alerts and audit trails: Receive immediate notifications for security events and maintain detailed logs of all access attempts. These records are vital for investigations and compliance.
- Open architecture and scalability: Choose systems that integrate with other technologies and can grow with your business, whether you're adding doors or entire construction sites.
- Multi-factor authentication (MFA): Add layers of protection for high-security areas by requiring a combination of credentials, such as a card and a PIN or a mobile credential and a fingerprint.
- Integration with CCTV and alarms: Connect your access control to Video Surveillance & Security Cameras to trigger recording on entry and link with alarms for unauthorized attempts.
- Contactless access: Use facial recognition, Bluetooth, or passive sensors for a hygienic, frictionless user experience that also reduces hardware wear.
The Primary Benefits of Implementing Controlled Door Access Systems
The advantages of controlled door access systems go beyond basic security to transform daily business operations.
- Improved security with granular control: Specify exactly who can access which areas and when. For example, grant a project manager 24/7 access while limiting contractors to specific zones during work hours, protecting equipment and sensitive information.
- Eliminating lost key risks: Instantly deactivate lost or stolen credentials from the management software, avoiding expensive rekeying and security breaches. A new card or mobile credential can be issued immediately.
- Operational efficiency: Automate access to let employees and contractors move smoothly through your facility without manual check-ins. This is especially valuable on construction sites with multiple crews.
- Effortless compliance and audit trails: The system automatically generates detailed logs of all access events, satisfying regulatory requirements and simplifying audits with clear, timestamped evidence.
Implemented thoughtfully, these systems become strategic tools that improve both security and operational effectiveness.
Installation and Maintenance Best Practices
Proper planning, professional execution, and ongoing care are critical for a successful controlled door access system.
- Site assessment: A thorough assessment is the foundation. It involves understanding security needs, mapping entry points, and evaluating infrastructure, especially for dynamic environments like construction sites.
- Professional installation: This is essential due to the complexity of integrating hardware, software, and networking. Professionals ensure compliance, proper wiring, and optimal system configuration.
- System testing: Before going live, installers verify connectivity, power, and user authentication. A reader installation typically takes 30-60 minutes, while software setup can take 2-5 hours.
- User training: Your team must know how to use their credentials and follow security protocols. Trained employees are your first line of defense.
- Maintenance agreements: Protect your investment with preventive care to ensure reliable performance and catch potential issues early.
- Security culture: A strong security culture, built on clear policies and training, ensures the technology delivers its full potential as part of a comprehensive strategy.
Frequently Asked Questions
When businesses across Texas start exploring controlled door access systems, we hear many of the same thoughtful questions. These concerns usually revolve around cost, convenience, and practical benefits. Let's explore the most common questions to help you make an informed decision.
How much does a typical commercial access control system cost?
The cost of a controlled door access system varies based on the number of doors, hardware type, and software model (cloud vs. on-premise). A small office trailer has different needs than a large commercial building, and the complexity of your setup impacts the investment.
Typical cost ranges for major components:
- Complete system: $2,000-$10,000 (most costs are for door equipment)
- Electronic locks: $50-$1,200 per door
- Readers and controllers: $100-$3,500 each
- Annual software licensing: Around $600 per year
- Ongoing maintenance: $0-$50 per door per month (depending on service agreement)
Modern systems are scalable, allowing you to start with essential doors and expand as your business grows. Construction companies often secure a main office first, then add job site trailers later. For an accurate quote, we recommend a consultation to assess your unique requirements.
Can I really use a smartphone to open up doors?
Absolutely. Mobile credentials are a reality for businesses across Texas, turning smartphones into secure digital keys using built-in Bluetooth and NFC technology.
When you approach a reader, it recognizes your phone's credential and grants access. The benefits are significant:
- Convenience: Employees use the device they already carry, eliminating the need for separate key cards or fobs.
- Cost Savings: Businesses avoid the expense of printing, issuing, and replacing physical cards.
- Remote Management: Instantly issue or revoke credentials for contractors or employees from anywhere, which is ideal for managing multiple job sites.
- Improved Security: Mobile credentials leverage a phone's built-in security like passwords or biometrics, creating multiple layers of protection.
Given that 85% of Americans own smartphones, this technology is accessible to nearly everyone and is especially useful for construction companies with rotating crews.
How do controlled door access systems improve building safety and convenience?
Controlled door access systems dramatically improve both safety and daily operations.
For safety, they offer:
- Lockdown features: Instantly secure your entire facility with a single command during an emergency.
- Detailed tracking: Create an accountability trail showing who entered where and when, which is invaluable for investigations.
- Restricted access: Effortlessly keep unauthorized personnel out of hazardous areas, a key benefit for construction sites. Integration with our Security Services provides comprehensive protection.
For convenience, they provide:
- Keyless entry: Eliminate the cost and hassle of lost keys and rekeying.
- Temporary access: Issue time-limited credentials for visitors and contractors that expire automatically.
- Remote door control: Grant access from a reception desk or a smartphone, improving operational efficiency.
These systems create a more secure environment while streamlining authorized access for everyone.
Conclusion: Making the Right Choice for Your Texas Business
Selecting the right controlled door access system is a critical business decision. It's about creating a security foundation that streamlines operations, grows with your company, and provides peace of mind.
This guide covered the essential components, from hardware and credentials to software. We compared cloud and on-premise solutions and highlighted the key features that improve daily use.
The key is matching the system to your actual needs. A small construction office has different requirements than a company managing dozens of job sites across Texas. The right system should support your future growth, whether you're expanding to new locations or taking on larger projects.
Integration is also crucial. Your controlled door access system should work with your video surveillance and alarm systems to create a comprehensive security ecosystem.
At VIA Technology, we help Texas construction companies and other businesses make these decisions. We understand the unique challenges of managing job sites, securing equipment, and maintaining compliance. Our approach is to design integrated technology solutions that make your operations easier and more secure.
We handle everything from site assessment and design to installation, training, and ongoing support. With our 24/7 monitoring and comprehensive project management, you can focus on your business while we manage your security.
Ready to improve your security and operational efficiency? Learn more about our Access Control solutions and find out how we can help you implement the perfect system for your business.


